Windows Authentication in IIS with Kerberos.NET
The last few samples I created for Kerberos.NET were all run from a console application. This served a couple purposes. First, the samples are a lot more portable this way; second, IIS doesn’t get in the way.
IIS supports kerberos authentication natively through the Windows Authentication mode. It does this via an ISAPI module that intercepts application response codes and does the negotiate dance on behalf of the application. This means as an application developer I can just say “return 401” and IIS appends a WWW-Authenticate header and processes any responses outside the sights of my application. This isn’t necessarily what we always want. Sometimes we want control over the request. The problem of course is that we can’t touch the ISAPI module — it’s too low in the request pipeline and it has final say over requests.
I always had it in my mind that this ISAPI module will always intercept the WWW-Authenticate/Authorization Negotiate header and strip them out of the request regardless of whether its enabled or not. At the very least these headers weren’t accessible when it was activated. This was the reason I didn’t create any samples for IIS hosting — it would be too much of a pain to figure out how to get it working (insofar as I couldn’t be bothered to figure it out right now).
It turns out I may just be remembering wrong. I was trying to limit the paths in which Windows Auth was going to be invoked the last time I tried futzing with it in IIS (such that a 401 would only invoke the WWW-Authenticate header at a given arbitrary path). As it turns out that required the module to be enabled and active. The module is not invoked if it’s turned off.
Sometimes I’m not very smart.
Well, in any case, the previous samples work just fine when hosted in IIS. I’ve created a web project just for this. Just make sure the Windows authentication mode is disabled and the authentication mode in the web.config is either not set, or set to None.
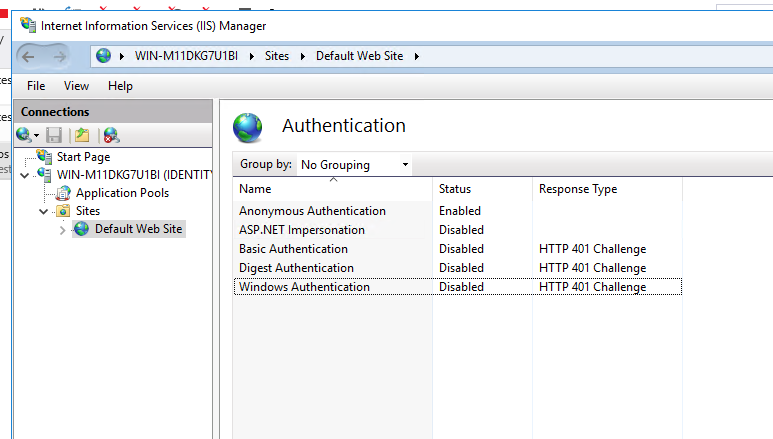
Just say no.
It’s also probably not a bad idea to just uninstall the Windows Authentication feature from IIS entirely:
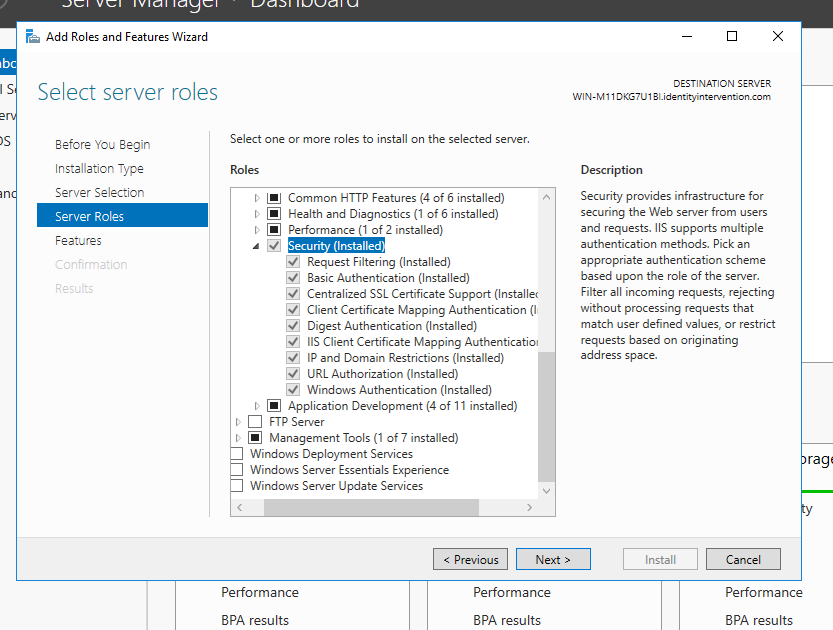
Just say no-no!
Remember kids: memory is volatile — just because you remember it one way doesn’t mean that’s actually how it is. 