Active Directory Claims and Kerberos.NET
Active Directory has had the ability to issue claims for users and devices since Server 2012. Claims allow you to add additional values to a user’s kerberos ticket and then make access decisions based on those values at the client level. This is pretty cool because you normally can only make access decisions based on group membership, which is fairly static in nature. Claims can change based on any number of factors, but originate as attributes on the user or computer object in Active Directory. Not so coincidentally, this is exactly how claims on the web work via a federation service like ADFS.
Of course, claims aren’t enabled by default on Windows for compatibility reasons. You can enable them through Group Policy:
Computer Configuration > Policies > Administrative Templates > System > KDC > KDC support for claims, compound authentication and Kerberos armoring
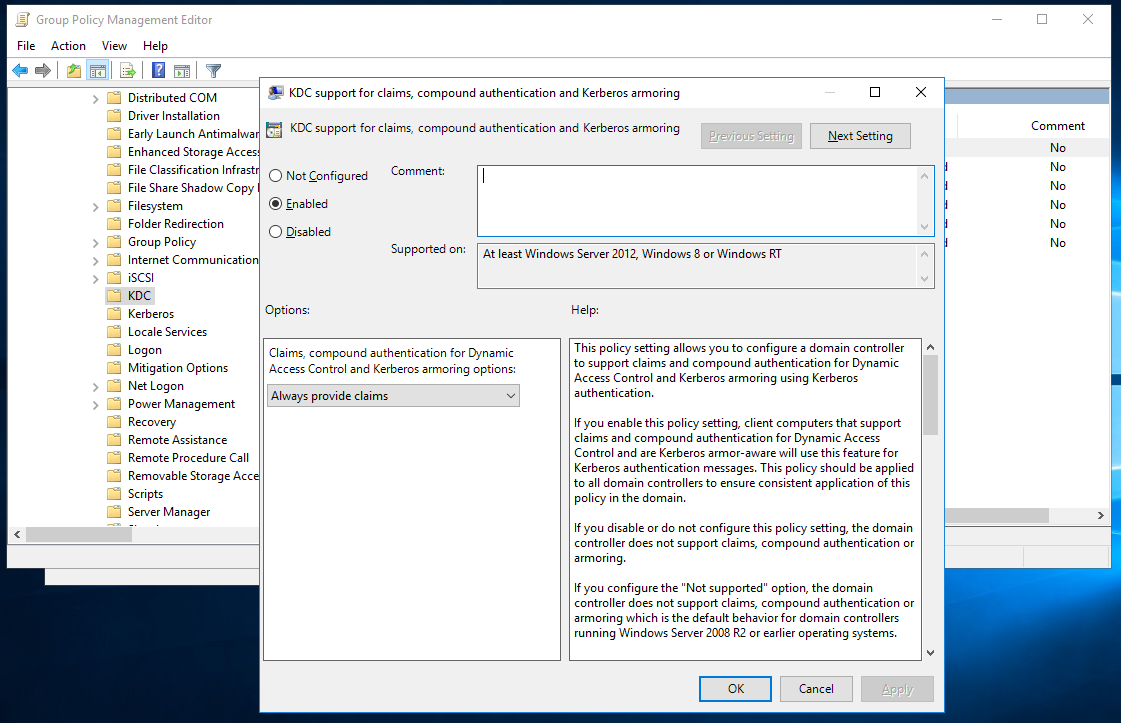
Allow Claims in Group Policy
You can configure claims through the Active Directory Administrative Center Dynamic Access Control.
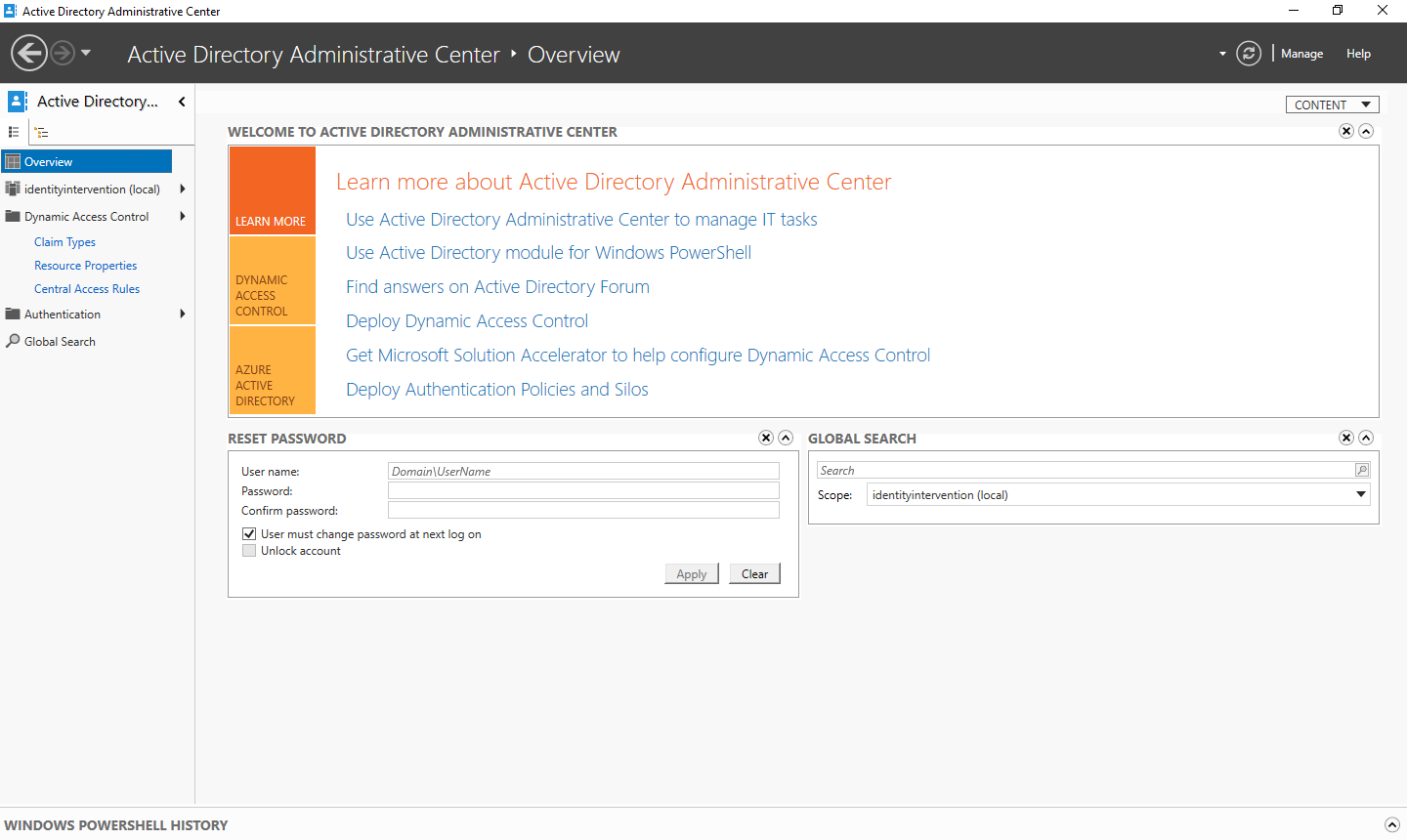
Active Directory Administrative Center Dynamic Access Control
You can see the Claim Types option on the left hand menu. From there you can add a claim by hitting the New > Claim Type menu.
The configuration is pretty simple. Find the attribute of the user or device you want to issue, and select whether it should be issued for users or computers or both. You can configure more advanced settings below the fold, but you only need to select the attribute for this to work.
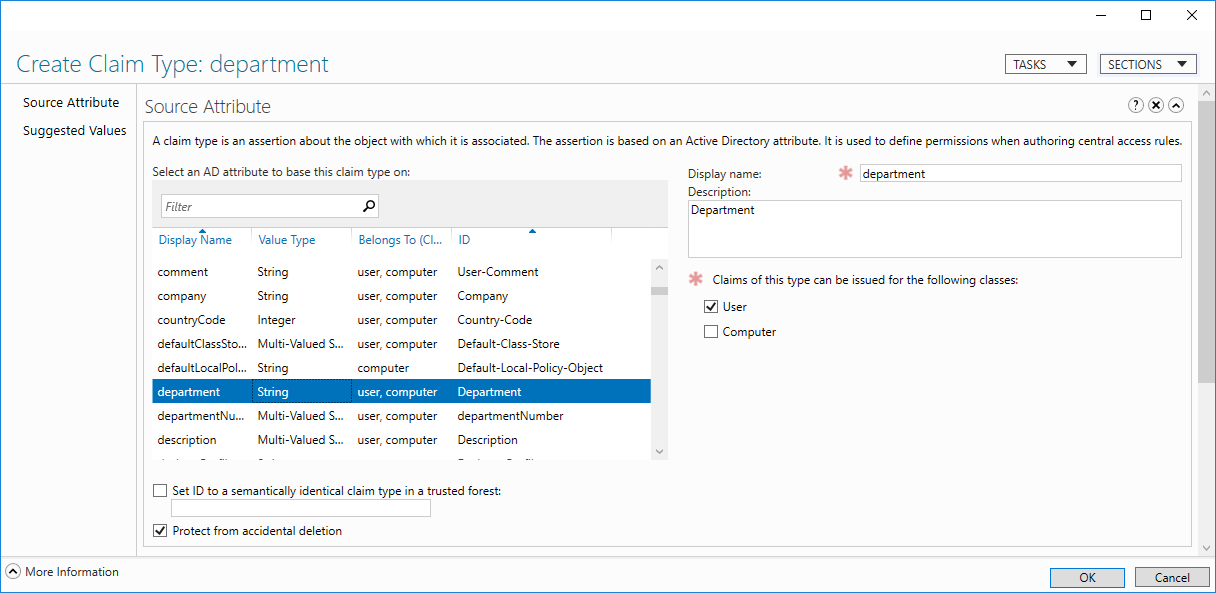
Add New Claim Type
Once the claim type is configured you can modify attributes of a user through the Attribute Editor in either ADAC or the AD Users and Computers console.
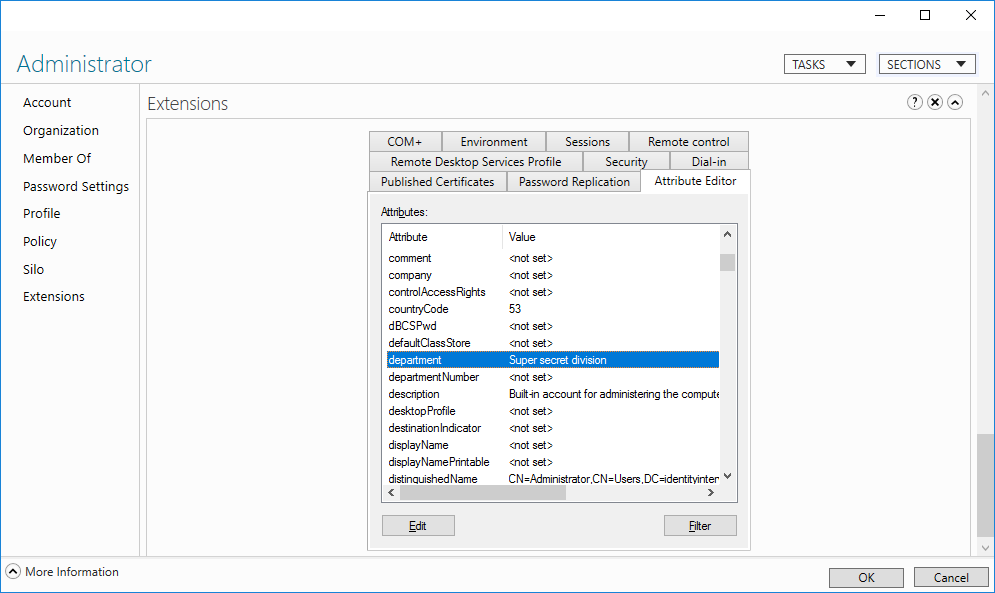
User Attributes in ADAC
That’s all it takes to get use claims. You do have to sign out and back in before these claims will take effect though since Active Directory issues claims in the Kerberos tickets, and the tickets are only issued during sign in (or the myriad other times it does, but sign out/in is the most effective).
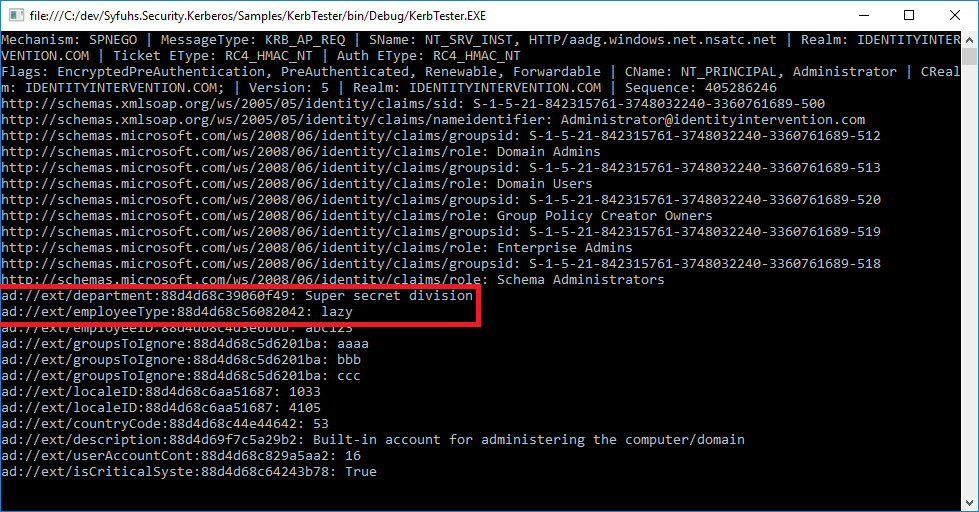
However, once you’ve signed out and back in you can pop open PowerShell and see the claims in your token:
[System.Security.Principal.WindowsIdentity]::getcurrent().claims | fl type, value Type : ad://ext/department:88d4d68c39060f49 Value : Super secret division
Windows 8 and higher automatically extract the claims from the PAC in the ticket and make them available in the user token. Additionally, .NET understands claims natively and can extract them from the Windows token.
And of course now Kerberos.NET! The library will automatically parse any user or device claims and stick them in to the resultant claims produced during authentication:
Kerberos Claims
No configuration necessary. The library will do all the work. Enjoy!