KDC Proxy for Remote Access
This proxying capability is useful for remote workloads that don't have line of sight to a Domain Controller.
Important Note: Because this product was originally designed and built to be used with services like RDP Gateway and DirectAccess [and SMB QUIC for Ned], official support is limited to installation and operation of those two services. If you plan on using this service outside of that scope I recommend reaching out to the Microsoft support teams or product groups to confirm supportability for any mission critical services.
As such, this post should not be taken as official guidance from any product group.
The gist of this service is that it's a web listener that sits on https://+:443/kdcproxy and relays messages to a Domain Controller. Clients are enlightened to know that a proxy exists and if all else fails try and communicate over that instead. This can be used when you need clients to authenticate with a Domain Controller for things like authentication or password changes but don't have a VPN in place or don't want to expose external clients to Domain Controllers directly.
The KDC Proxy was originally built for services like RDP Gateway and DirectAccess, but these days it's looking to be more useful for general remote authentication.
Here's how you deploy it.
Server Deployment
First, you need a domain-joined server. It needs to at least have a public network interface with a domain name pointed to it. Clients will connect to it over the internet. Networking-wise you can just forward port 443 if necessary.
You will need to create a trusted certificate for the public domain name of the proxy endpoint.
Domain: corp.identityintervention.com
DC: dc01.corp.identityintervention.com
KDC Proxy: proxy.identityintervention.com
The proxy service is already present on the server, but not configured to start.
Configure Server
The service needs to be configured before it can be started.
- Start an elevated command prompt and configure a URL ACL for the endpoint.
netsh http add urlacl url=https://+:443/KdcProxy user="NT authority\Network Service" - Associate the certificate created previously with the endpoint (this tells HTTP.SYS to use the certificate when you connect over HTTPS). Note that for
appidyou should generate a random GUID here (from PowerShell try[Guid]::NewGuid()). The certhash is the thumbprint of your certificate.netsh http add sslcert ipport=0.0.0.0:443 certhash=aaaabbbbccccddddeeeeffff0000111122223333 appid={aaaaaaaa-bbbb-cccc-dddd-aaaabbbbcccc} - If you're not using smart card certificates (or Windows Hello) for authentication you should disable the certificate authentication requirement.
REG ADD "HKLM\SYSTEM\CurrentControlSet\Services\KPSSVC\Settings" /v HttpsClientAuth /t REG_DWORD /d 0x0 /f - Additionally if you're not using certificates you need to enable password authentication.
REG ADD "HKLM\SYSTEM\CurrentControlSet\Services\KPSSVC\Settings" /v DisallowUnprotectedPasswordAuth /t REG_DWORD /d 0x0 /f - Configure the KDC Proxy Service (KPSSVC) to start automatically.
sc config kpssvc start=auto - Finally you can start the service.
net start kpssvc
The service should start without issue.
Configure the Client
Clients need to be enlightened to use a KDC Proxy. This can be done through GPO or through modifying the registry directly. The GPO path is:
Administrative Templates\System\Kerberos\Specify KDC proxy servers for Kerberos clients
Enabling this policy requires setting Realm-to-Value mapping. The realm is your domain name (corp.identityintervention.com as I used aboved) and the value is specially crafted.
<https proxy.identityintervention.com:443:kdcproxy />
If you're using a custom path or port you can specify it explicitly above, otherwise you can leave them empty and the client will fill in the rest:
<https proxy.identityintervention.com />
With this policy deployed give the client a reboot (or wait a while -- there's some caching that goes on) and try to log in. You should find users are now authenticating over the KDC proxy endpoint.
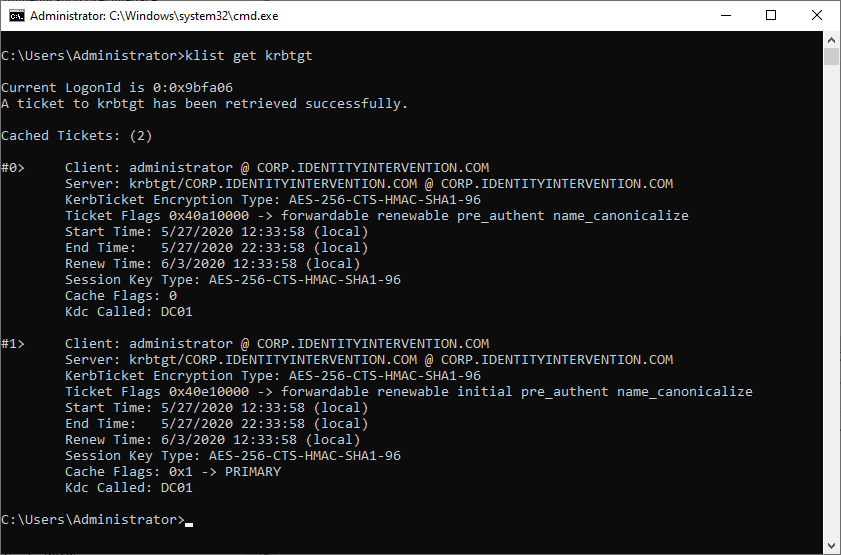
To verify, from a logged in session launch a command prompt and try the following command:
klist get krbtgt
You should see a ticket or two show up.
Registry Settings
On the off chance you're stuck trying to deploy these settings on a machine that can't pull down group policy updates, you can manually configure the registry keys for the client:
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System\Kerberos]
"KdcProxyServer_Enabled"=dword:00000001
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System\Kerberos\KdcProxy\ProxyServers]
"corp.identityintervention.com"="<https proxy.identityintervention.com />"
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System\Kerberos\Parameters]
"NoRevocationCheck"=dword:00000000
Password Change
Password changes should work through the normal CTRL+ALT+DEL "Change a password" screen.
Troubleshooting
Standard events are collected throughout the lifetime of the service and can be viewed in Event Viewer under the system log as well as the Kerberos-KdcProxy\Operational logs.
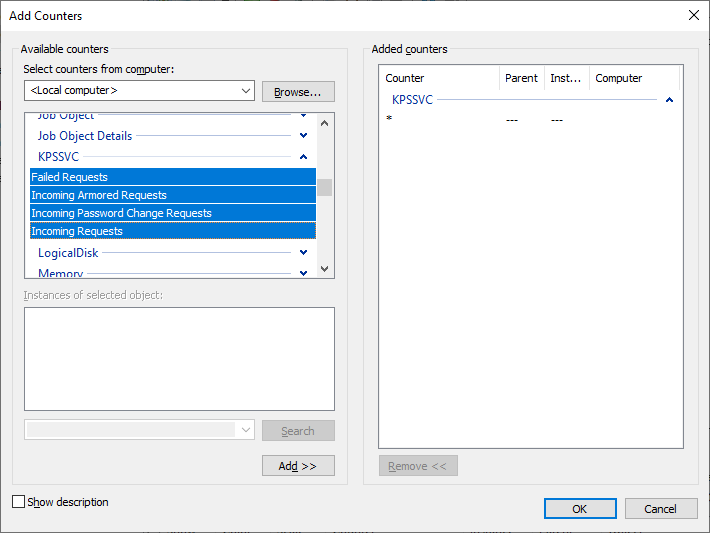
There's also a set of performance counters for the service under the KPSSVC counter group.