Protecting Against Credential Theft in Windows
Have you ever thought to yourself "boy, I sure wish I had to use passwords more often"? No, of course not. Passwords suck. Good passwords are long and hard to remember and easy to remember passwords aren't good. They're inherently portable and easy to steal.
— Steve Syfuhs (@SteveSyfuhs) February 12, 2021
Twitter warning: Like all good things this is mostly correct, with a few details fuzzier than others for reasons: a) details are hard on twitter; b) details are fudged for greater clarity; c) maybe I'm just dumb.
We've known this a great many years and platforms like Active Directory and Windows have supported better options like smart cards for 20 years because of this. So what is it about passwords that make them so hard to protect?
First of all, we need them to be random. Random means people can't guess them. Suppose I pick a simple 5 letter password from the lowercase alphabet. That's 26 letters and 5 positions, or 26^5, or ~11.8 million combinations.
As a human it'll take you forever to guess it, but it'll take a computer less than a second to generate all 11.8 million combinations. But I'm also human so I'm going to pick something easy for me to remember: "riley". That's super easy to guess if you've looked me up.
So we start to enforce strength requirements: must be 8 characters with uppercase, lowercase, numbers, symbols, one reoccurring character from season 6 of your favorite TV show. This gives you (say) 92 characters and 8 positions or 92^8 or 5132 trillion combinations.
So my password is now aSdX3$CC;^k@. I can barely remember what I had for lunch yesterday, am I expected to remember this? Oh, and I have to change it every 90 days? Ugggggh.
But it turns out this is equally easy for a computer to guess anyway, so. 🤔
Ever wondered what a #hashstack @hashcat cluster of 448x RTX 2080s could do for #password #cracking? How about 31.8 TH/s on NTLM, 17.7 TH/s on MD5 pic.twitter.com/k9DmxSULBz
— Terahash (@TerahashCorp) July 27, 2019
Of course, suppose you don't have $30k to drop on a password cracking rig and you don't have benefactors that will donate to the cause, brute-forcing your way through is out of the question. So you attack the next best thing: Windows.

To attack Windows you have to understand how authentication works in Windows. In simple terms you have a high value credential (password) which you exchange for a medium value credential (TGT/PRT), that is exchanged for low value credentials (service tickets/access tokens).
You can think of them as first order, which derives a second order, which then derives a third order credential, all with decreasing capabilities as you go further out. This is sort of the mantra for solutions like Credential Guard: protect the first and second order credentials.
That's all well and good however technologies like Credential Guard serve very specific and well defined purposes and aren't holistic catch-all solutions.
This is important: there's never a one-size-fits-all solution to security.
Securing complex systems like Windows, or your enterprise network, requires many layers. It's like the swiss cheese analogy for stopping the spread of COVID-19. Layer one stops something very specific. Layer two stops another thing, layer three... etc.
So Credential Guard protects your 1st and second order credentials at rest *once* they've entered the system. To understand why this matters it's important to go back to how credentials are processed by Windows.
Passwords enter your computer through credential providers, into LSA, and processed by AD or AAD. I've explained this in great detail in both text and video form. What Happens When you Type Your Password into Windows? (syfuhs.net)
Cred provs do their thing and pass it off to LSA.
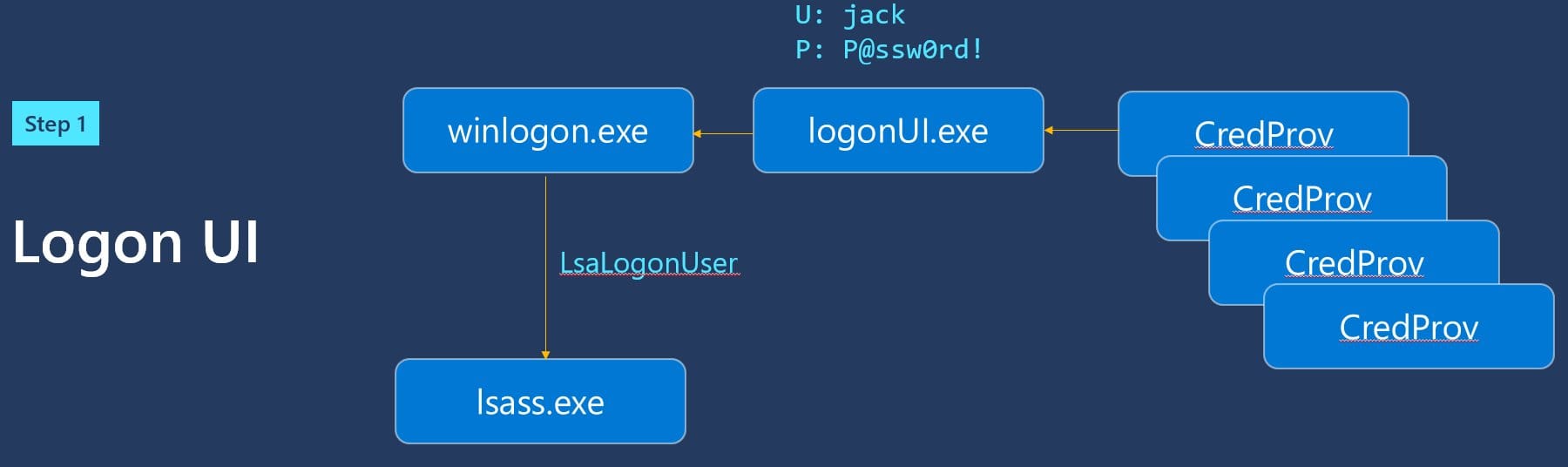
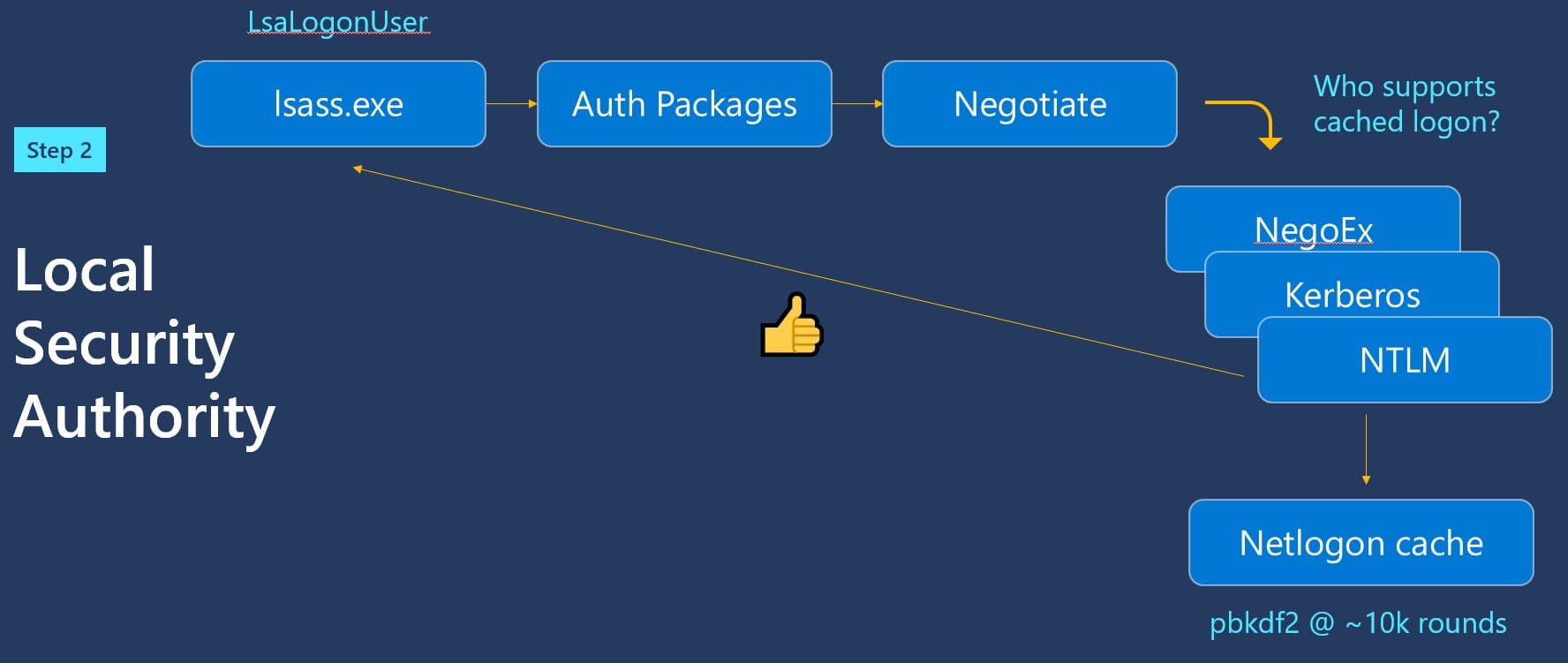
LSA does a cached logon.
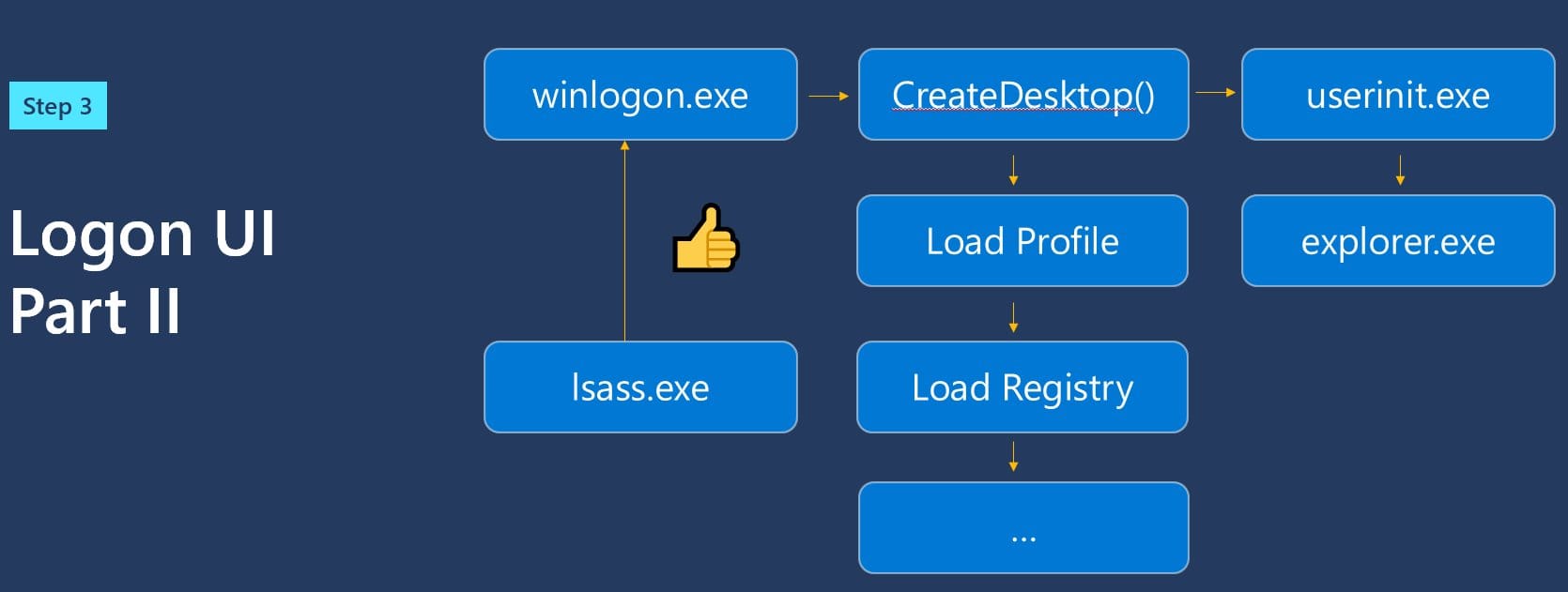
You're taken to your desktop.
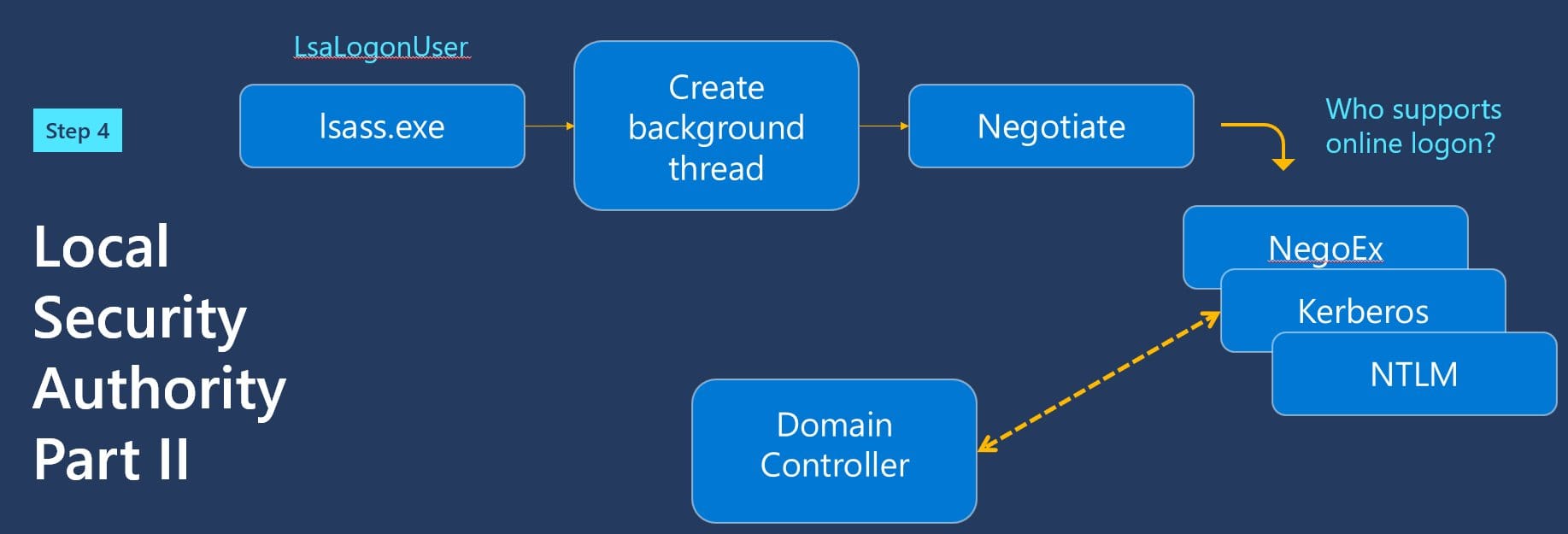
And THEN off you go to Active Directory or AAD.
But this is all very hand-wavy. Along the way there are built-in extensibility points where third parties can add in their own code to make the login work however they need it to, because sometimes that's just how things be.
You can drop in your own credential provider that looks just like the password credprov. You can install a custom LSA authentication package that listens for passwords. Or you can install a subauth module and log the password.
But we have solutions for that. LSA Protected Process mode is one. It prevents anyone from loading third party code into LSA so they can't touch those extensibility points. But you can bypass LSAPPL -- so we have HVCI to enforce it. Lots of solutions here.
But there's more to this. Your password doesn't magically go from your keyboard to the credprov. It gets converted to electrical signals and sent along a wire into your computer to be processed by the CPU in a driver in the kernel and then converted back to text.
