Examining Kerberos Messages with Fiddler
I recently created a Fiddler extension based on the Kerberos.NET library that lets you examine Kerberos messages within web requests and responses.
You can install it today: https://github.com/dotnet/Kerberos.NET/releases. All you need is to download setup.exe and run it (note it's not signed as of this post, that's on the TODO list).
It's pretty simple to use. First, go install it. Then launch Fiddler, then navigate to a website that you know uses Kerberos (or more likely Windows Integrated Auth/Negotiate).
Reading Messages
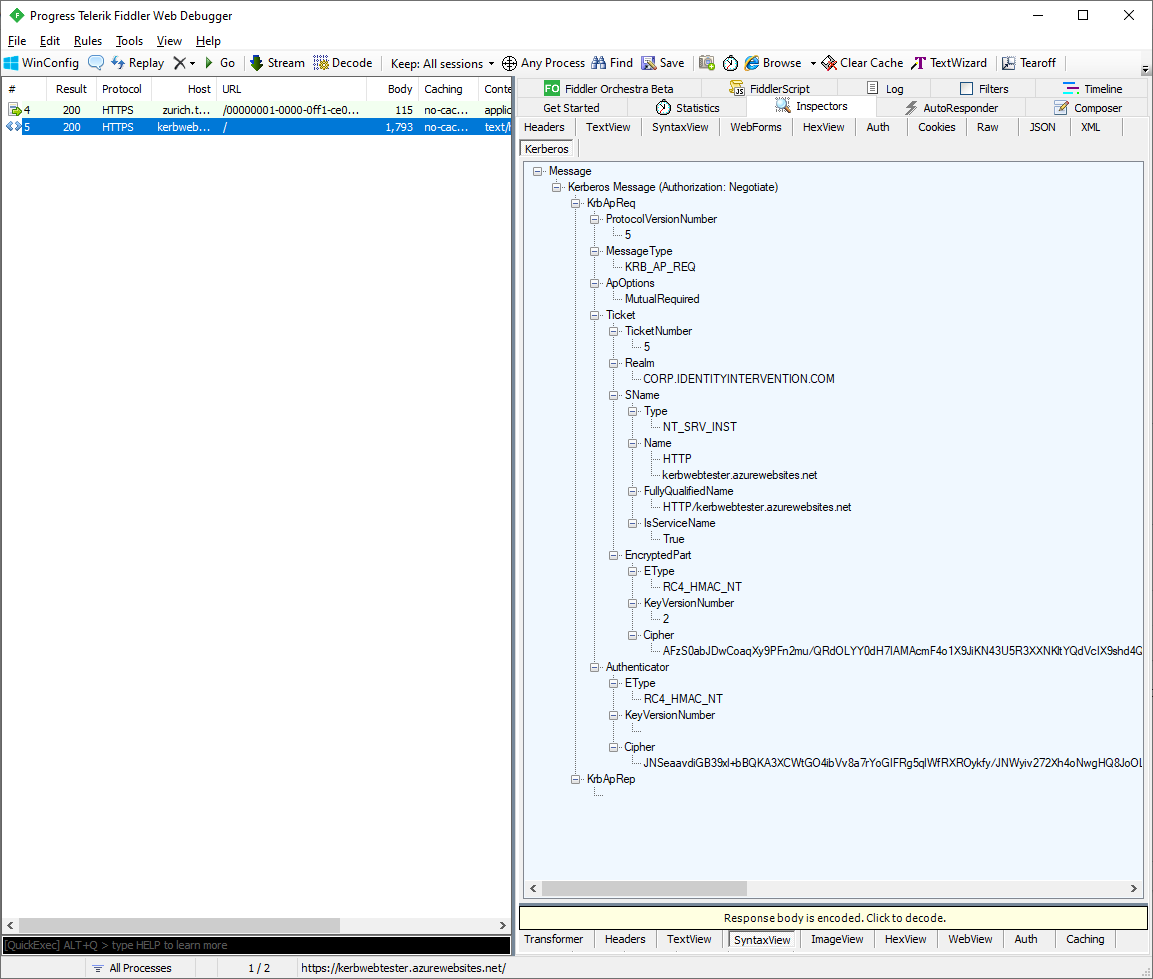
From there an inspector is added that will read the Authorization: Negotiate YII... header. Select the "Kerberos" inspector and you'll be presented with a tree view that lists all the properties of the message.
The properties represent the raw wire format. Certain properties support additional processing like encrypted fields that let you decrypt their value:
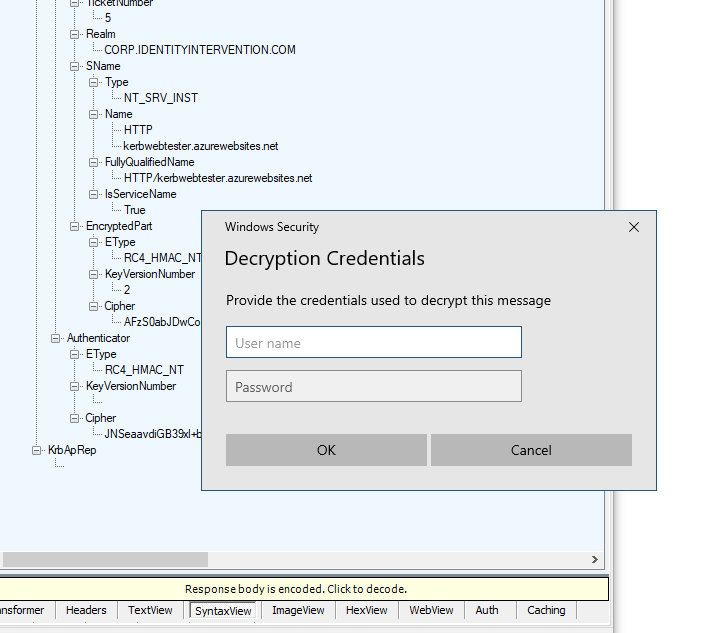
There are a couple ways this can work. If you have the final derived key you can paste it into the password field as a base64-encoded value. Note that username field does need some value. It's a work in progress. The second way is to provide a fully-qualified username into the username field, and enter the password into the password field, and the inspector will derive the key manually from those values.
The decrypted message is then loaded into the tree view for review.
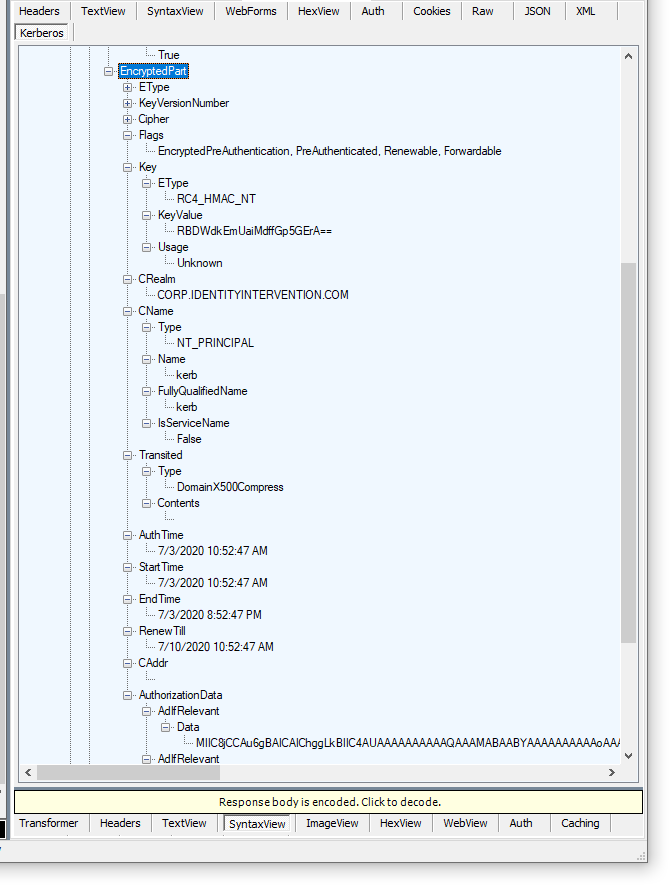
Additional fields like authorization data can also be processed further. For example, the PAC data (where group membership is stored) can be parsed through the ad-if-relevant sequence.
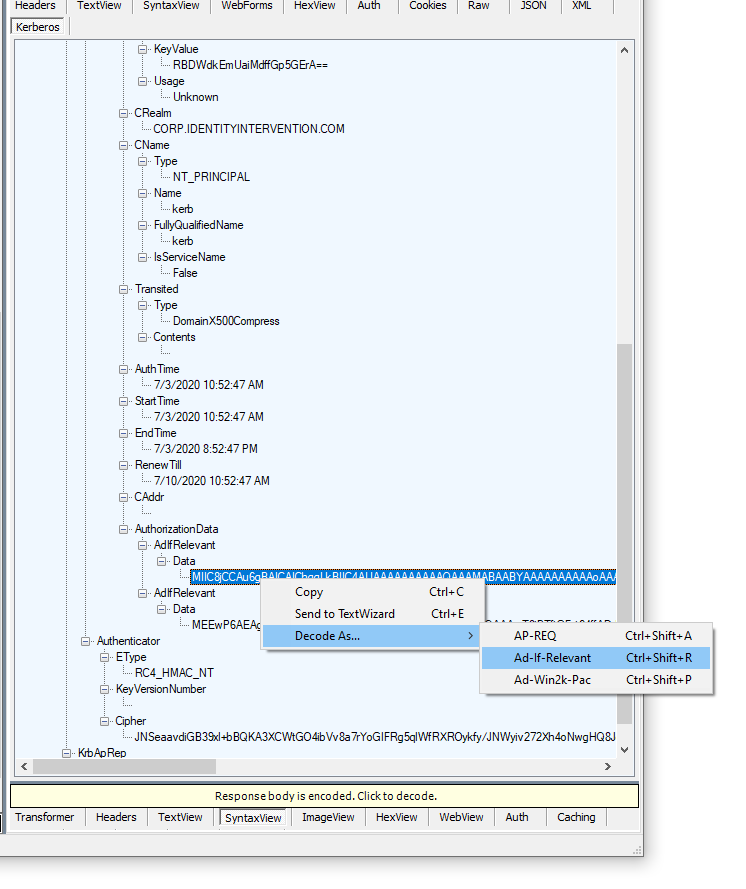 And then parse the PAC itself (yes, it really is ad-if-relevant / ad-if-relevant / ad-win2k-pac).
And then parse the PAC itself (yes, it really is ad-if-relevant / ad-if-relevant / ad-win2k-pac).
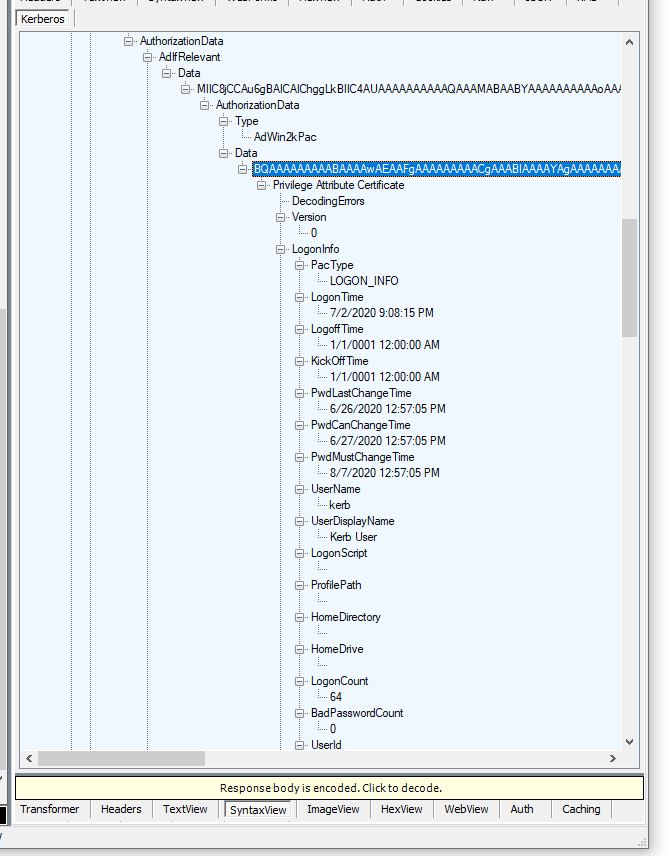
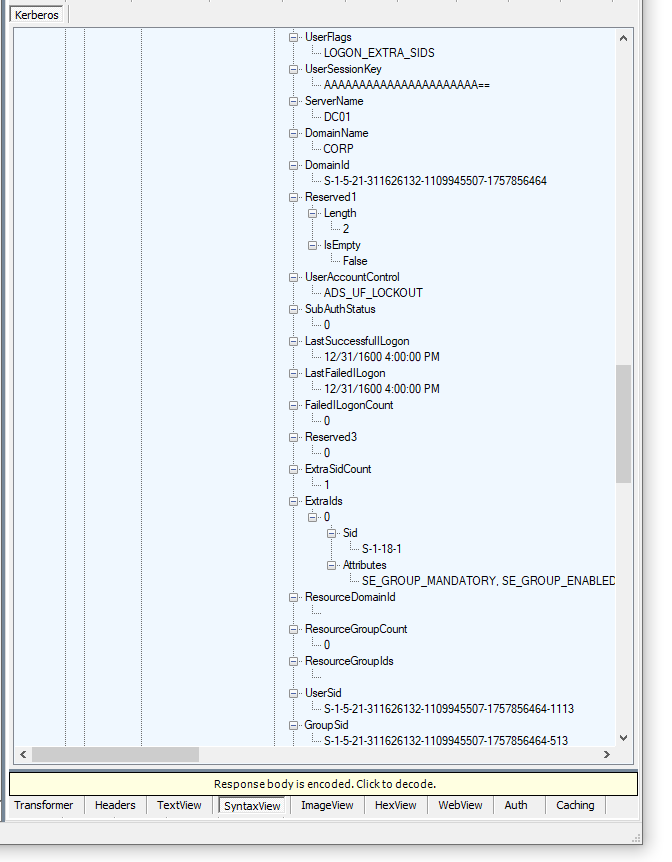
The PAC structure represents all the group memberships and additional SIDs that the KDC includes during logon.
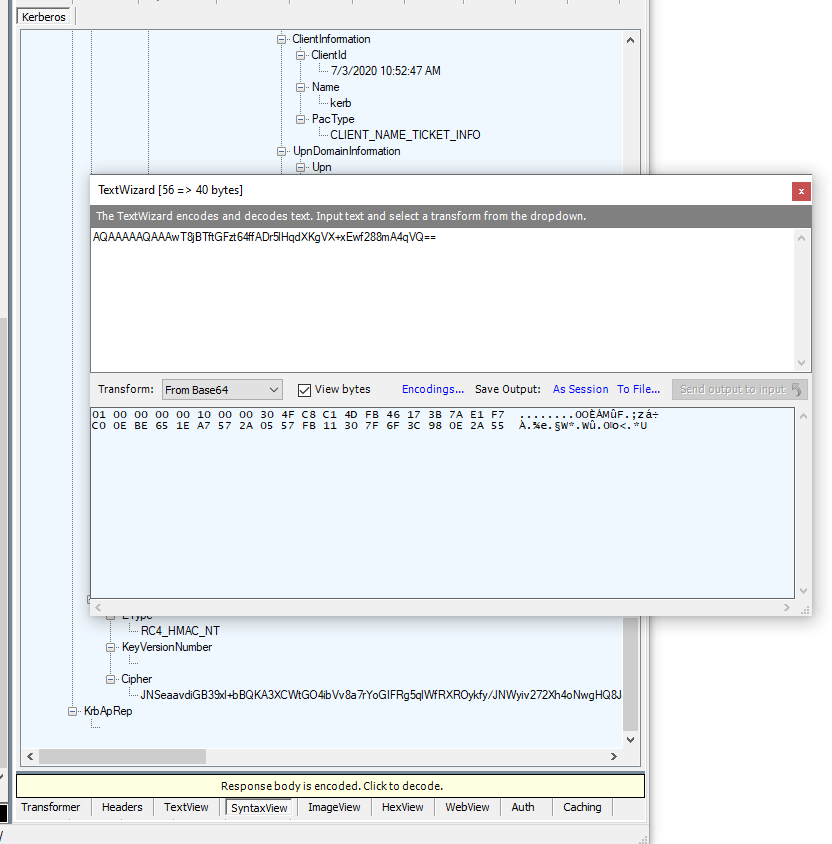
While you're at it you can send the property values to the TextWizard for additional processing.
Reading KDC Proxy Messages
A little known feature exists in Windows (and other Kerberos libraries) that lets you tunnel Kerberos messages destined for a KDC through an HTTPS Proxy instead of over port 88 via TCP or UDP. This feature is called the KDC Proxy.
Normally you would use a tool like Wireshark to inspect KDC traffic, however since this is proxied over HTTPS you can't use Wireshark without a lot of configuration to decrypt traffic. This inspector now lets you easily review these messages without all the hassle.
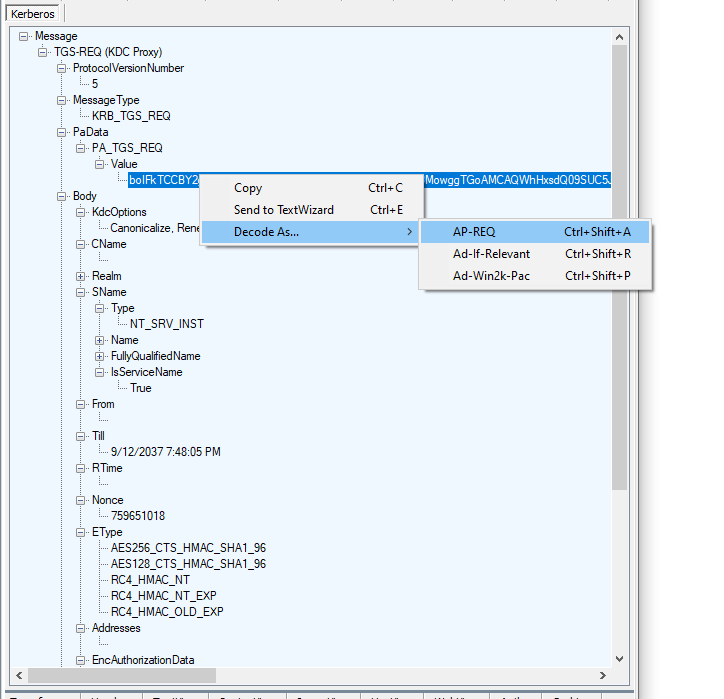
You can see the client request to the KDC.
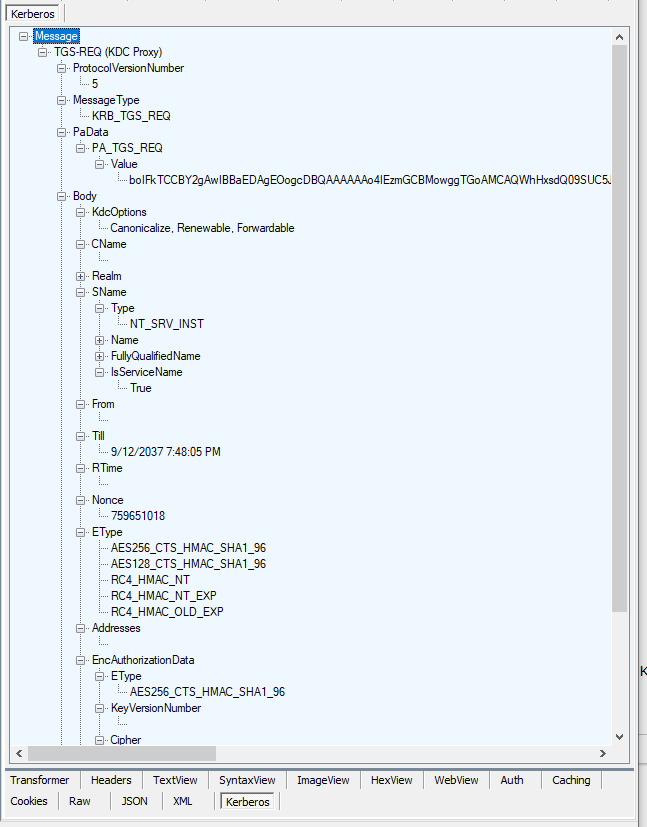
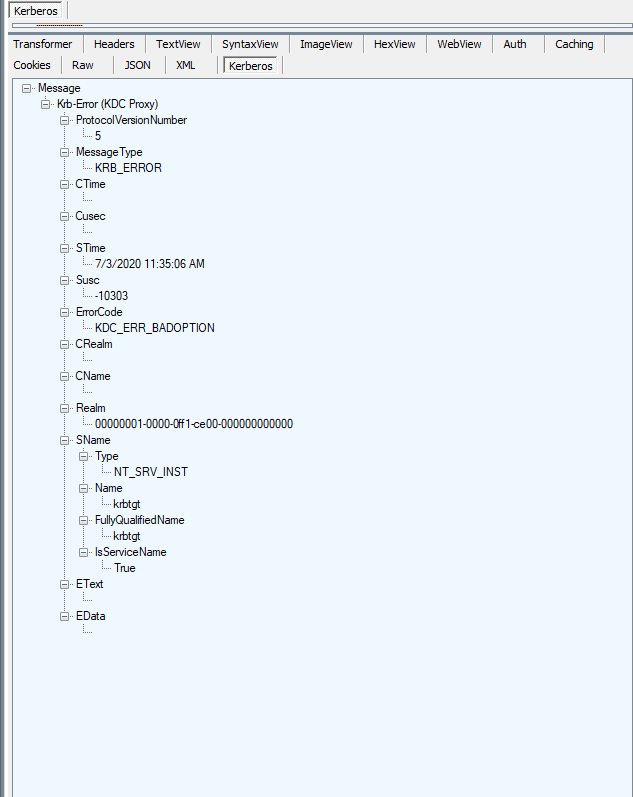
And the KDC's response.
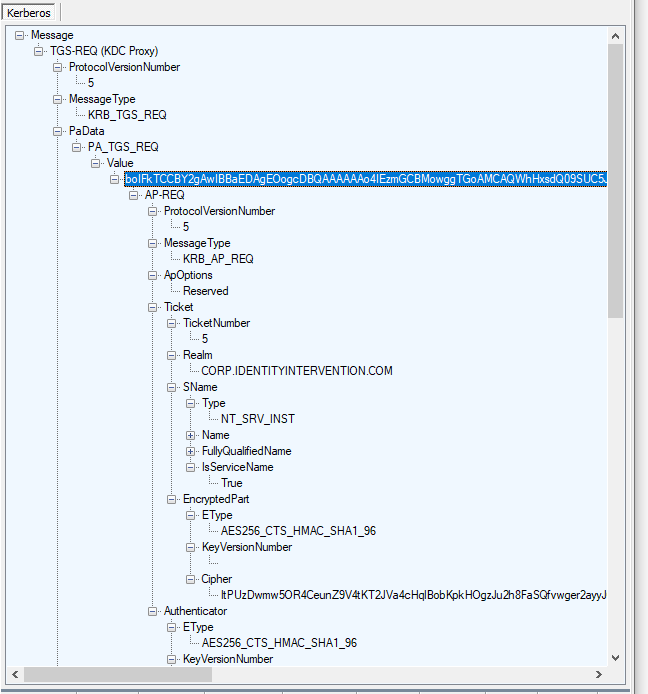
And just like the other properties you can decode parts of the message further, such as looking at the AP-REQ in the TGS PA-Data.
That's it! That's the tool. Enjoy! Please log any bugs you find on the GitHub Issues.